Overcoming the Challenges of Legacy Identity Governance and Administration (IGA)
The Evolution of IGA Solutions
Identity Governance and Administration (IGA) solutions were initially developed to manage identities across a limited set of critical internal applications. These early solutions were designed during a period when organizations had fewer and relatively centralized systems with clearly defined permission structures.
They were effective at handling user roles, permissions, and access controls for essential internal systems.
As enterprises increasingly adopted cloud-based platforms, the scope of IGA tools expanded significantly. Complex cloud systems, such as SAP or Salesforce, became a standard part of the landscape, each with their intricate permissions, roles, and dependencies.
The adoption of cloud technologies introduced complexities that traditional IGA systems had to evolve to manage.

However, today’s organizational environments have drastically changed from the early days of IGA. Modern enterprises experience exponential growth in their application landscapes, primarily driven by SaaS adoption, specialized software tools, and evolving business practices. Organizations often utilize a broad range of highly specialized applications to fulfill even simple operational workflows.
For example, a straightforward business process like payment processing could involve over a dozen distinct software solutions. Unfortunately, most of these solutions remain invisible or unmanaged by traditional IGA systems, leaving significant gaps in identity control.
Core Limitations of Traditional IGA: Disconnected Applications
The primary limitation of legacy IGA solutions is their inability to scale to the number of applications in use within modern enterprises. Typically, organizations manage to integrate approximately 10 to 20 new applications into their IGA systems annually.
Yet, ERP systems indicate that the actual number of purchased applications is often in the thousands. This disparity creates a significant visibility gap. At the current integration rate, it would take decades to gain comprehensive control over all enterprise applications.
This situation leads us directly to the concept of disconnected applications—applications not integrated into the IGA ecosystem for several reasons:
- Legacy/Internal Applications: Complex, custom-built applications with lengthy integration roadmaps due to technical constraints and resource limitations.
- Organizational Barriers: Applications managed independently by different business units, subsidiaries, or geographic regions, often as a result of mergers and acquisitions.
- Access Sprawl: SaaS applications rapidly adopted by end-users without formal IT oversight, resulting in uncontrolled proliferation.
- Technical Limitations: Applications lacking essential technical capabilities for integration, such as APIs for managing users, roles, or deprovisioning. In other cases, APIs may exist but require expensive licensing tiers, which organizations choose not to adopt.
Individually, each scenario presents significant operational challenges; collectively, they severely undermine traditional IGA initiatives, particularly in the face of increasing identity-based cyber threats. This combined impact necessitates a reevaluation of traditional IGA strategies.
Symptoms of Disconnected Applications in Enterprises
Enterprises experiencing the impacts of disconnected applications often face clear operational symptoms:
- Overloaded IT and Helpdesk Teams:
- IT teams spend excessive manual effort managing basic tasks such as access requests, role changes, and deprovisioning through tickets, scripts, or spreadsheets.
- Constant backlog issues arise, significantly slowing IT responsiveness and reducing operational efficiency.
- IT teams spend excessive manual effort managing basic tasks such as access requests, role changes, and deprovisioning through tickets, scripts, or spreadsheets.
- Employee Frustration and Shadow IT:
- Users find access management processes unclear and slow, leading to frustration and delays.
- Employees frequently bypass official IT channels, adopting unauthorized solutions to avoid administrative delays. This behavior substantially increases organizational risk.
- Users find access management processes unclear and slow, leading to frustration and delays.
- Compliance and Access Review Overload:
- Compliance teams become overwhelmed and selectively review only a fraction of critical applications, compromising comprehensive compliance efforts.
- Significant administrative overhead is created during access certification processes, burdening distributed teams and managers who must participate in frequent reviews.
- Compliance teams become overwhelmed and selectively review only a fraction of critical applications, compromising comprehensive compliance efforts.
By the way, we provide a practical guide to help you conduct your access reviews.
Adopting a Modern Approach: Zygon’s Light IGA
Addressing these challenges requires a modern approach specifically designed around disconnected applications. Zygon’s approach begins by rapidly building a comprehensive view of applications, users, and identities across the enterprise.
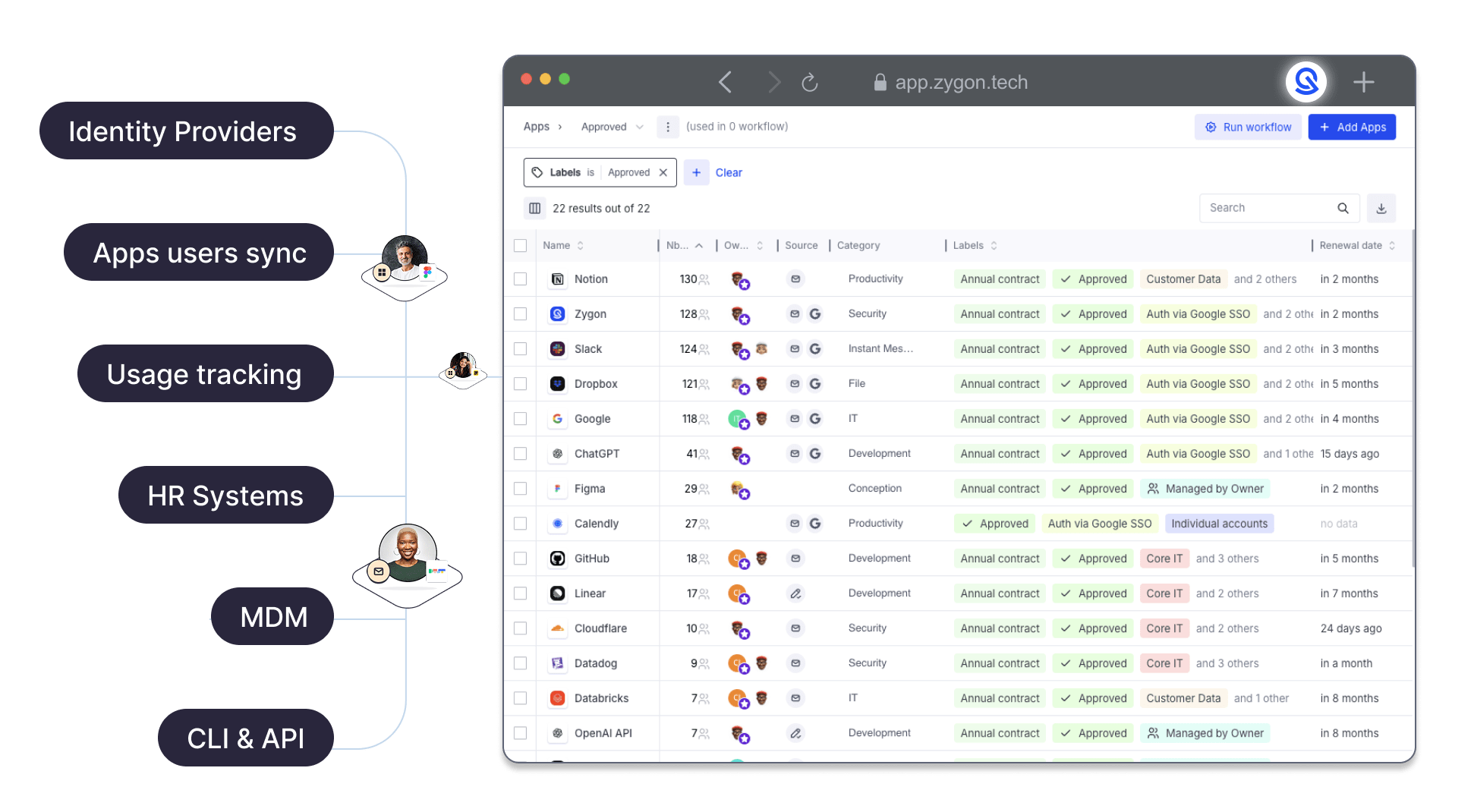
Integration When and Where It Matters:
- Core Identity and HR Systems: Zygon integrates with essential identity providers (IDPs) like Microsoft Entra, Active Directory, Okta, Ping Identity, One Identity, Google Workspace, and HR systems such as ADP, BambooHR, and HiBob.
- Existing IGA Platforms: Seamless integration with solutions like SailPoint and Saviynt.
- Messaging Platforms: Integrations with Slack, Microsoft Teams, ensuring notifications reach employees effectively.
- IT Systems: Automatic ticket creation in ITSM and service desk systems, and integration with monitoring and alerting tools to trigger security notifications.
Continuous Discovery and Inventory Management:
- Rather than static data imports, Zygon employs continuous discovery methods, dynamically identifying both known and unknown applications, assessing their usage and criticality.
- This continuous discovery approach significantly reduces shadow IT, improving visibility and management.
Centralized Data Repository and Standardized Data Model:
- Zygon maintains a standardized, centralized repository of identities, enabling quick access to vital information (user identities, access methods, roles, login activity).
- Advanced dynamic filters facilitate complex queries to gain insights across users and applications.
Scalable Automation and Customizable Workflows:
- Bulk actions and automated policies apply uniformly across the entire inventory, ensuring consistency.
- Highly customizable workflows adapt precisely to enterprise-specific requirements, avoiding rigid, cookie-cutter solutions.
- Role mining tools standardize role assignments and permissions, providing insights for administrators and security teams.
Tailored, User-Friendly Interfaces:
- Zygon recognizes the diversity of its user base—from highly technical infrastructure teams requiring APIs and CLIs to business users needing intuitive, straightforward interfaces.
- Simplified portals streamline access request processes, reducing friction and enhancing adoption.
- Zygon Copilot, an AI-powered browser extension leveraging computer vision, dramatically simplifies routine tasks for end-users, accelerating adoption without operational disruption.
A Balanced, Efficient Solution
Zygon’s modern IGA solution is designed to complement existing infrastructures seamlessly by integrating disconnected applications effectively.
With robust integrations, dynamic discovery, centralized data management, automation, and tailored user experiences, enterprises can achieve enhanced agility, security, and alignment within their complex, evolving digital landscapes.
Struggling with user access reviews?
Get your free guideFAQ
All the questions you can have
Explain the concept of "disconnected apps" in the context of IGA
While many applications are registered through procurement and listed in an ERP or other dedicated systems, these methods often fail to manage identities or evaluate the business criticality of these applications effectively.
This situation is best captured by the concept of "disconnected applications", which underscores identities that are neither managed within an Identity Governance and Administration (IGA) solution nor adequately maintained in your identity provider or SSO solution.
These unmanaged apps are still awaiting integration or lack SCIM support, preventing unified access from a single pane of glass. This is one of the key challenges that Zygon aims to address.