What’s Broken With Access Requests
Access requests are supposed to make it easy for employees to get the tools they need, when they need them—without compromising security or compliance. But in most organizations, they’re still deeply flawed.
Ask any IT or security team managing identity governance today, and you’ll hear the same frustrations: fragmented systems, poor user experience, lack of visibility, and growing access sprawl.
Even worst, access sprawl incurs significant costs for your organization.
Let's explore what’s fundamentally broken with access requests, and how to fix it.
Access Requests Are Still Stuck in the Helpdesk Era
For many organizations, access requests are still managed manually—through ticketing platforms like JIRA, ServiceNow, or even shared inboxes. A user needs access to an app, submits a ticket (if they know where to do it), and then waits.
Sometimes the ticket gets routed to the right team. Sometimes it gets stuck in a queue. Sometimes the user bypasses the whole system and asks a colleague or manager directly, just to move faster. Yes, but…
This approach introduces several problems.
First, it’s inconsistent. The process changes depending on the application, the team, or the requestor’s knowledge of internal systems. There is no single, standardized way to request access across the organization.
Second, it’s opaque. There’s rarely a full audit trail. Who approved the access? When? For how long? Was there a justification? In most cases, you won’t find the answer unless someone digs through old tickets or email chains.
Worse, these legacy systems often only cover a narrow set of applications—typically the ones officially integrated or approved by IT. But in modern environments, that’s only a small fraction of what’s actually in use.
Employees now rely on dozens, sometimes hundreds, of SaaS apps that are introduced bottom-up, team by team. End users often create identities on-the-go, unaware of the security risks involved.
A recent trend has emerged where sensitive corporate information is being fed to AI agents, further exacerbating these risks.
Anthropic refers to this as "agentic misalignment" in this well-documented research.
Business teams manage access informally, and IT loses visibility.
This is the real problem.
What Good Looks Like: The New Standard for Access Requests
A modern access request system isn’t just a form with a submit button. It’s a layer of governance that ties identity, application ownership, and security policies together—without slowing users down.
The most advanced organizations are moving toward systems that are seamless, complete, and adaptive. Here's what that looks like in practice.
1/ The experience must be “unified”
There should be a single place where employees go to request access to any application in use—whether it's fully automated, partially managed by IT, or owned by a business team.
From the user's point of view, it shouldn't matter how access is technically provisioned or who manages the app. They just need a simple, reliable workflow.
If that workflow is different for every app, people will default to asking around or skipping the process altogether.
The governance model breaks down at the first point of friction.
2/ The system should be complete
This means going beyond pre-configured catalogs of "official" applications. Employees often need access to tools that are not yet known to IT—either because the application is new, niche, or introduced at the team level.
In a good system, when a user requests access to an unknown app, this should not be treated as an exception. Instead, it becomes a discovery opportunity.
The platform should recognize the request, trigger a security review, and potentially onboard the application into the governance framework.
This closes the loop between access and visibility, instead of letting shadow IT grow unchecked.
3/ Approval workflows must be flexible and role-aware
Not every app is owned by IT. In fact, many SaaS tools—especially in marketing, design, product, and legal—are managed by business units.
These owners should be able to receive, review, and approve access requests without involving IT unnecessarily.
But that doesn’t mean bypassing governance. The request, the approver, the justification, and the access duration should all be logged centrally.
Flexibility for approvers shouldn’t come at the cost of traceability.
4/ The access request experience must be contextual
Expecting users to find the right request portal or workflow is unrealistic—especially for occasional needs or first-time users.
The best systems meet users where they are. That could mean surfacing an access prompt directly in the browser when the user tries to reach an app they don’t yet have access to. Or integrating with tools like Slack to let users make a request without breaking context.
The key is to reduce friction to the point where compliant behavior is the default, not the exception.
5/ Don’t let technical aspects hinder the process
Security teams are well aware of this issue and are equipped to handle it. However, the complexity of deploying and integrating existing solutions is surpassed by the identity sprawl.
Zygon changes this dynamic with continuous monitoring, SCIM-less provisioning, and CLI option.
This approach enables the deployment of identity governance projects at scale in a matter of days, rather than the months or even years typically required for legacy IGA systems.
This shift—from fragmented, manual access flows to unified, adaptive systems—is the real frontier in identity governance.
How Zygon Approaches This Differently
Zygon is a modern IGA platform built with a more aggressive stance on completeness, usability, and real-world adoption.
Our approach is focused on three things:
- Collapsing all access flows into a single system
- Surfacing requests where users actually work
- Continuously expanding what IT sees and governs
Here’s how we do it:
- Access requests for every application, not just IT-managed ones
Zygon supports access requests for any app in use—whether it's integrated, manually provisioned, or managed by a business team.
We don’t limit functionality to a pre-approved catalog. This includes apps with no SCIM or API, internal tools, and external SaaS adopted by departments.
Learn more about our SCIM-less approach
- Automatic routing to the right approver
Whether an app is owned by IT, security, or a specific team lead, Zygon dynamically routes the request to the right stakeholder.
No more guessing or escalation chains. The platform handles delegation based on actual app ownership.
.webp)
- Justification and time-bound access built in
Users are prompted to provide context and duration. This enables automatic expiration of entitlements and supports security audits out of the box—without requiring custom policy coding or external workflows. - Requests directly in the browser where users work
Zygon can prompt users in real time when they try to access an app they don’t have access to—no need to switch tools, portals, or look up processes.
This improves adoption and helps close the gap between policy and behavior.
- Capture of unknown apps through requests
When someone asks for access to an app not currently tracked, Zygon logs the app, creates a placeholder record, and notifies IT.
This turns organic requests into a discovery pipeline, helping IT stay ahead of shadow IT.
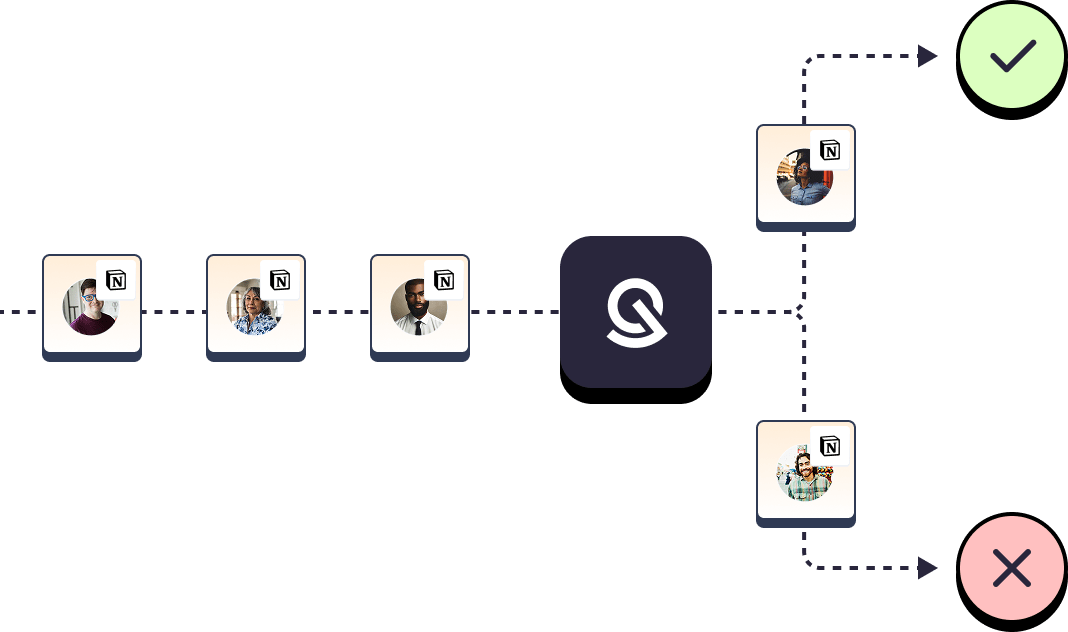
- Unified audit trail for all access flows
Every request—whether fulfilled via automation, manual approval, or delegated access—is logged in a central timeline.
This gives you a complete, organization-wide picture of who requested what, who approved it, and when access was granted or removed.
In short, we treat access requests not as a feature, but as the front door to identity governance.
It's where visibility starts, where user behavior can be nudged toward compliance, and where IT regains control—not by locking things down, but by enabling smarter workflows for everyone.
More importantly, Zygon is Built to Integrate, Not Replace
Zygon isn’t here to rip and replace your existing stack. In most enterprise environments, identity governance isn’t greenfield.
IT teams already have provisioning scripts, approval workflows, and ticketing systems in place—usually with a lot of time and effort behind them.
That’s why Zygon is built to integrate seamlessly into your current ecosystem.
.webp)
If your IT team uses JIRA to manage access to certain applications, Zygon can generate the relevant JIRA tickets automatically. From the end user’s point of view, the access request feels unified and consistent.
But behind the scenes, Zygon respects and extends your existing workflows, ensuring IT retains control where it’s already established.
If your company has automated provisioning in place—through platforms like Okta, SailPoint, or Microsoft Entra—Zygon doesn’t replace it. Instead, it triggers these systems where possible, and fills the governance gaps where they can’t reach.
This includes applications without APIs, tools that don’t support SCIM, or long-tail SaaS managed by business teams. Zygon ensures that every app is governed—whether it’s tightly integrated or completely disconnected.
This is what makes Zygon effective in the real world: it brings governance and visibility to 100% of your application landscape, while complementing the automation and control mechanisms you’ve already built.
We’re not trying to change how IT works—we’re making it work better, across more of the environment.
See It for Yourself
Access requests don’t have to be fragmented, slow, or blind to what’s really happening in your organization. With Zygon, you get a unified system that covers all your applications, reaches users where they work, and brings full visibility back to IT and security.
We've released a self-service option so that you can experience Zygon firsthand. See for yourself!
FAQ
All the questions you can have
Access Requests refer to the process by which individuals or systems seek permission to access specific resources, data, or areas within an IT environment. These requests are a fundamental part of "Access Control", that regulates who or what can view or use resources.
Access requests can occur in various scenarios for the IT department. Zygon often refers to Employee Onboarding (a new employee needs access to the company's email system, internal intranet, and project management tools) but other use case include Privileged Access, JIT access, etc.


Stop wasting time on access reviews
Get Zygon's powerful and versatile workflows set up in minutes!
Start for free