Identity Governance in the Modern Enterprise: Why HRIS Data Is No Longer Enough
For years, HR Information Systems (HRIS) have served as the authoritative source of identity data inside companies.
If someone had access to internal tools or appeared on an org chart, it was because they existed in the HRIS.
That model made sense when the only people working in a company were salaried employees, neatly structured into departments and reporting lines.
But that world is gone.
Modern organizations are more porous, dynamic, and interconnected than ever before. Contractors, freelancers, vendors, and partners all play active roles in delivering value.
And guess what? They all need access to internal systems.
As a result, the HRIS no longer reflects the full reality of who is inside your environment, what they do, and what they can access.
This evolution mirrors a broader shift in how IT operates. Just as the lines have blurred between corporate and personal devices, they’ve blurred between formal employees and other contributors.
In other words, identity is no longer something defined purely by HR or IT. It emerges from how people actually collaborate and what they actually do.
In this article, we’ll explore:
- Why HRIS data becomes less reliable over time
- How employees are just one part of a much larger identity ecosystem
- The real risks this gap creates in identity governance
- And what it takes to build a system that reflects the real picture, not just the org chart
HRIS: A Snapshot That Fades
At the moment of hiring, HRIS data tends to be quite accurate. The employee’s name, role, department, and manager are all entered as they have been pulled straight from the job posting or contract.
But from that point forward, reality starts to drift.
People evolve. Their responsibilities shift. They take on new projects, start supporting other teams, and build informal networks across the organization.
Yet these changes rarely get captured in the HRIS.
Take job titles.
The title someone was hired under might describe what they were doing on day one, but within six months it’s often outdated. They might be leading a team, driving cross-functional initiatives, or embedded in a different department altogether.
And none of which shows up in official records.
The same goes for reporting lines.
We regularly see HRIS data listing managers who no longer supervise the employee in any meaningful way.
Reorganizations, dotted-line relationships, or interim assignments all break the clean hierarchy that HRIS expects.
And then there’s the issue of departments.
Departments grow, split, or get renamed. But those changes don’t always propagate through every system, leaving people miscategorized for years.
What’s worse?
IT and security teams are often asked to make critical access decisions based on this data. But if the information is out of sync with the real world, those decisions are inevitably flawed.
One of the simplest and most effective ways to improve data quality? Show it to the people it describes, and let them fix it.
When employees or managers see outdated or inaccurate information, they usually want to correct it. The key is enabling that kind of bottom-up feedback loop.
More Than Employees: The Hidden Majority of Access
HRIS systems are built to manage employees. But in today’s enterprise, that’s no longer enough.
In many organizations we’ve worked with, less than 40% of digital identities belong to traditional employees.
The remaining majority is made up of people who contribute to the company’s mission in other ways—but don’t show up in HR systems.
Let’s break down who these people are.
Long-term contractors
These individuals often work alongside employees for months or years. They may have a company-issued email address, laptop, or Slack account.
From a systems perspective, they’re indistinguishable from full-time staff. Yet, they’re completely invisible in HRIS.
Short-term freelancers
Whether it’s a content writer, marketing consultant, or external developer, these people often need access to a narrow set of tools for a limited period of time.
They may never be assigned an official domain account, but they still hold sensitive access.
Partners, customers, and design collaborators
As companies become more integrated with their customers and partners, access boundaries get blurrier. External people are regularly invited into shared folders, design platforms, and product environments. Sometimes even with editing or admin rights.
In one recent case, an IT team believed access to a popular design tool was fully controlled through Okta. But upon deeper inspection, dozens of external contributors had been invited directly into projects, entirely bypassing centralized control. The problem wasn’t bad policy. No, it was “invisible collaboration”.
All of these identities create value. They help build products, close deals, support customers, and more. But if they’re not tracked and governed, they also introduce risk.
The Governance Gap: What You Can’t See Will Hurt You
When identity governance relies exclusively on HRIS data, it fails to reflect the real access landscape.
And that failure shows up in two critical ways:
1/ Incomplete visibility
If you only track identities from your HRIS, you’re missing a massive portion of users who have access to your systems.
That means when you perform access reviews or try to enforce least privilege, you’re working off an incomplete and misleading picture.
2/ Mismanaged permissions
Without a true view of who people are and what they’re doing, it’s impossible to make informed decisions about access.
Admin rights linger where they shouldn’t. Guest accounts remain active long after the project ends. And security teams are left chasing ghosts during audits.
These aren’t theoretical risks. They show up in breach reports, compliance failures, and operational blind spots.
From Static Org Charts to Collaborative Reality
To govern identities effectively, companies must stop pretending that top-down data tells the whole story.
Instead, they need to embrace a more dynamic, inclusive, and collaborative approach. One that captures both how things should work and how they actually do.
This is exactly what Zygon was built for.
Zygon doesn’t just integrate with your HRIS—it complements it. We bring together data from HR systems, identity providers, SaaS tools, and employees themselves to build a unified, accurate view of every user.
Here’s how:
1. Unify fragmented data
Zygon connects to multiple HRIS platforms, identity providers, and directories. Whether your org chart lives in Workday, your contractors are managed in Deel, or your domain identities sit in Google Workspace, we ingest and reconcile it all.
Explore Zygon’s integration directory and discover our CLI option.
2. Detect and highlight discrepancies
Our policy engine compares what’s supposed to be happening (from your official systems) with what is actually happening (based on real system access). When we see mismatches—like someone outside of HRIS with admin rights—we flag it instantly.
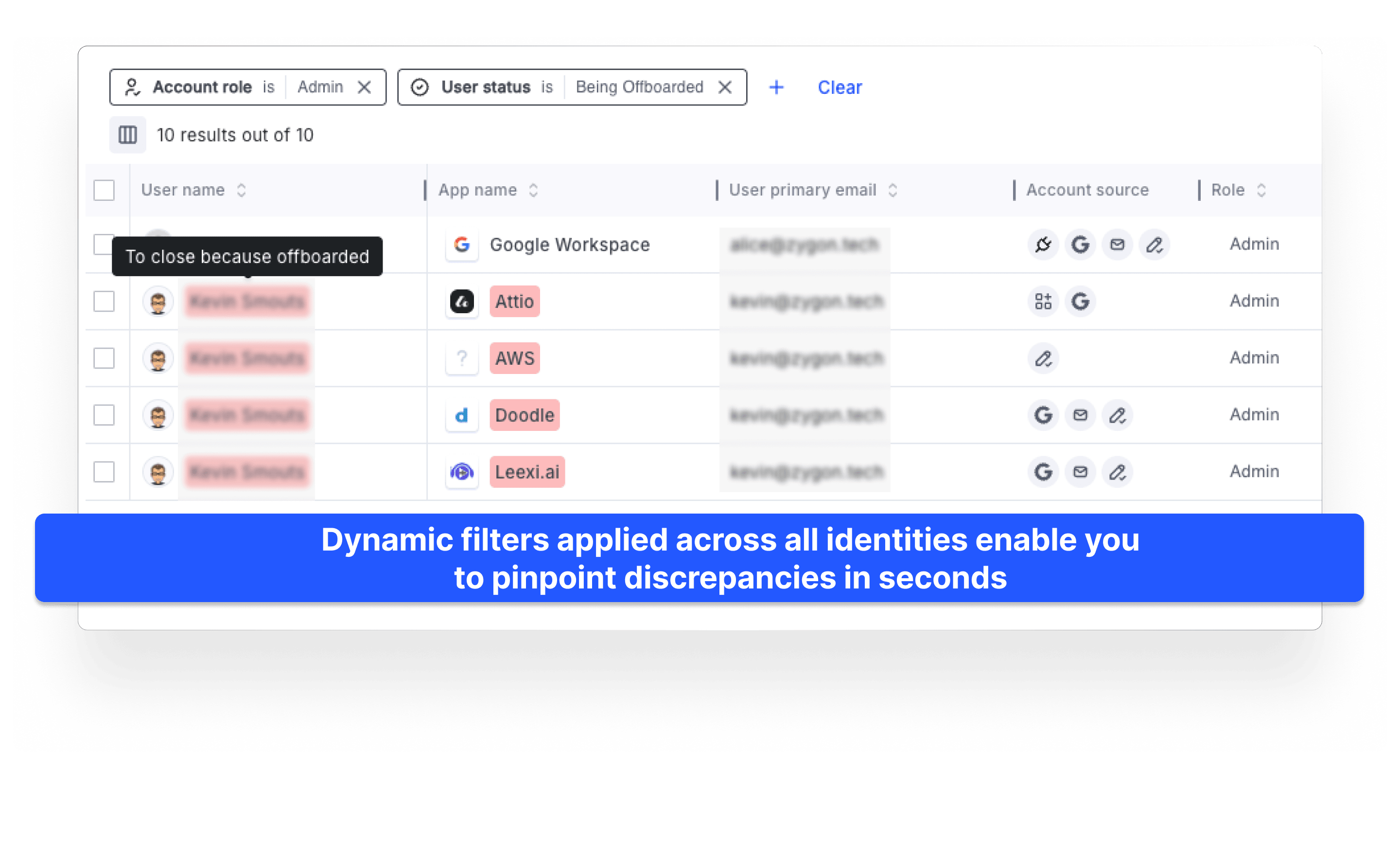
3. Scale collaboration
Zygon gives IT and security teams tools to collaborate with the rest of the business. Run campaigns, delegate reviews, and collect updates from managers or users themselves. No more spreadsheets. No more guesswork.
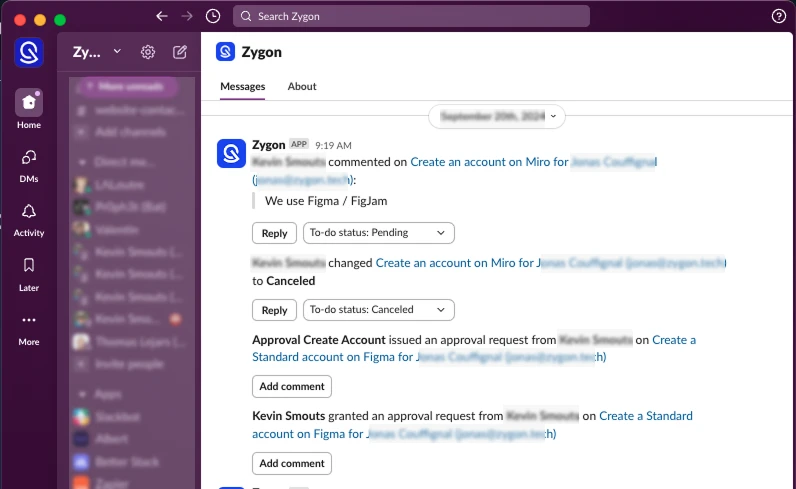
4. Embrace reality, not just policy
HRIS data is a model of how things should be. Zygon helps you capture how things are. And when those two diverge, we help you close the gap.
Final Thought: You Can’t Secure What You Don’t See
Identity governance isn’t just about managing employees anymore. It’s about managing everyone who touches your systems—employees, contractors, freelancers, and guests alike.
And to do that well, you need more than a static org chart. You need a real-time, flexible, collaborative platform that reflects the truth on the ground.
That’s what Zygon delivers.
After ensuring secure application access for human users, a new security challenge arises: managing the growing use of AI agents that collect data across multiple systems.. These agents also require identities to perform their tasks, and their number is exploding. For further insights on this topic, we recommend reading our dedicated post on managing Non-Human Identities (NHIs).
Struggling with user access reviews?
Get your free guideFAQ
All the questions you can have
What is an HR Information System? (HRIS / HCM)
HRIS solutions are designed to maintain, manage, and process detailed employee information and human resources-related policies and procedures. These systems typically include features such as time and attendance tracking, payroll processing, and benefits administration.
Another category of software, known as Human Capital Management (HCM), encompasses the functionalities of HRIS and extends its scope to include the acquisition, management, and optimization of the human workforce. HCM systems cover additional areas such as employee training, professional development, recruitment, and onboarding.
Example of HRIS solution include: Workday, Dayforce, Rippling, HiBob, Deel, Lucca...
Which HRIS data are relevant for Identity Governance?
Consider the importance of contract start and end dates, which are crucial for the seamless onboarding and offboarding of users. This information acts as a trigger to create accesses for a new employee joining the company. Upon their departure, it is essential to ensure that their access is not only deactivated but that all accounts are properly closed. Failure to do so can lead to significant security vulnerabilities. Additionally, overlooking this process can result in unnecessary licensing costs for the company.