IAM practitioners common struggles with Identity Governance solutions
Identity Governance is an ongoing journey. (who said never-ending? 😀)
This isn’t solely due to challenges like identity sprawl or the emergence of Non-Human Identities (NHIs) and Agentic AI.
No, it’s a continuous process because each organization faces unique, evolving factors such as distinct hosting environments, technology stacks, organizational structure changes, and varying regulatory constraints.
Nothing new, right?
But what is the consequence of this dynamic (and perpetual) process?
Well… IAM practitioners always need to recombine, reconfigure, rescript a castle that piles up. In other words, everyone struggles with Identity Governance.
We’ve chosen to highlight the most redundant or significant challenges our customers face at Zygon.
Good news #1: You are not alone!
Good news #2: We’ve racked our brains to get some solutions
Let’s dive in.
IGA solutions coverage is limited to just a fraction of apps
Don't get us wrong: we're not criticizing Saviynt, SailPoint, or even Okta! These major players are leaders for good reasons: they excel and deliver what their clients expect.
However, a project owner at a major energy company using Saviynt shared these insights with us:
- They have approximately 4,000 applications identified in their ERP system.
- Only 10% of these applications (400) were initially planned to be covered by Saviynt.
- Starting 4 years ago, only 120 applications had off-the-shelf integration capabilities.
- Until now, the integration process for new apps has been slow, averaging just about 20-25 new applications every year.
IAM teams keep on working hard to integrate internal and legacy applications into their IGA tool, believing it to be a necessity.
But is it really?
Not anymore. Light IGA serves as an effective intermediary solution, helping organizations bring those “disconnected apps” under control while they work towards full integration as per their roadmap.
Alternatively, you might find that having visibility and managing all identities from a single pane of glass is sufficient for your needs (who knows?)
However, this approach works best when application ownership is clearly defined—a topic that is continually evolving within every organization.
Is it a “Disconnected Apps” struggle or ownership confusion?
While most applications may be registered through a procurement process and listed in your ERP or dedicated system, this doesn't aid in managing identities or tracking the criticality of these apps to the business.
The concept of disconnected apps is the best we came up with to illustrate this situation: all these identities that aren’t in an IGA solution or well-managed into your identity provider.
But it’s not the only issue.
Organizations continuously evolve their policies to manage app ownership. Some still rely on on-premise software traditionally managed by the IT department. However, with the rise of cloud-hosted applications, ownership has shifted for certain apps, particularly those dedicated to departments like sales or marketing, where individuals within these teams often take charge.
Consider the real-life example of this company managing a marketplace: the engineering and infrastructure teams use multiple interconnected payment-processing tools. But only one of which is managed directly by IT.
Although these teams follow solid security practices, the gap arises because IT maintains knowledge of employee movements—departures, role changes—while the engineering teams do not consistently receive or act upon this information.
Our audit revealed that two of these critical payment systems still contained active accounts belonging to employees who had left over six months ago (!)
These accounts, lacking integration with SSO or centralized identity management, posed a significant security risk.
There's also the scenario where a company gets acquired and brings its own tech stack and organizational structure into the mix, transitioning to the acquirer's systems—sometimes only partially.
Also sometimes subsidiaries claim exceptions, we really feel for IAM practitioners…
Let's move past the examples and the mounting issues. What can we do about it?
How to bridge the gap created by these “disconnected apps”?
While there isn't a one-size-fits-all solution, you might find some options here to help you prioritize and address what feels most critical for your situation.
Detecting all disconnected apps in hybrid hosting environments
Imagine having real-time access to every identity, all from a single pane of glass. This is the capability that Zygon provides to IAM teams. See it as a complementary tool to your existing stack, acting as a centralized platform where anomalies can be swiftly detected and remediated.
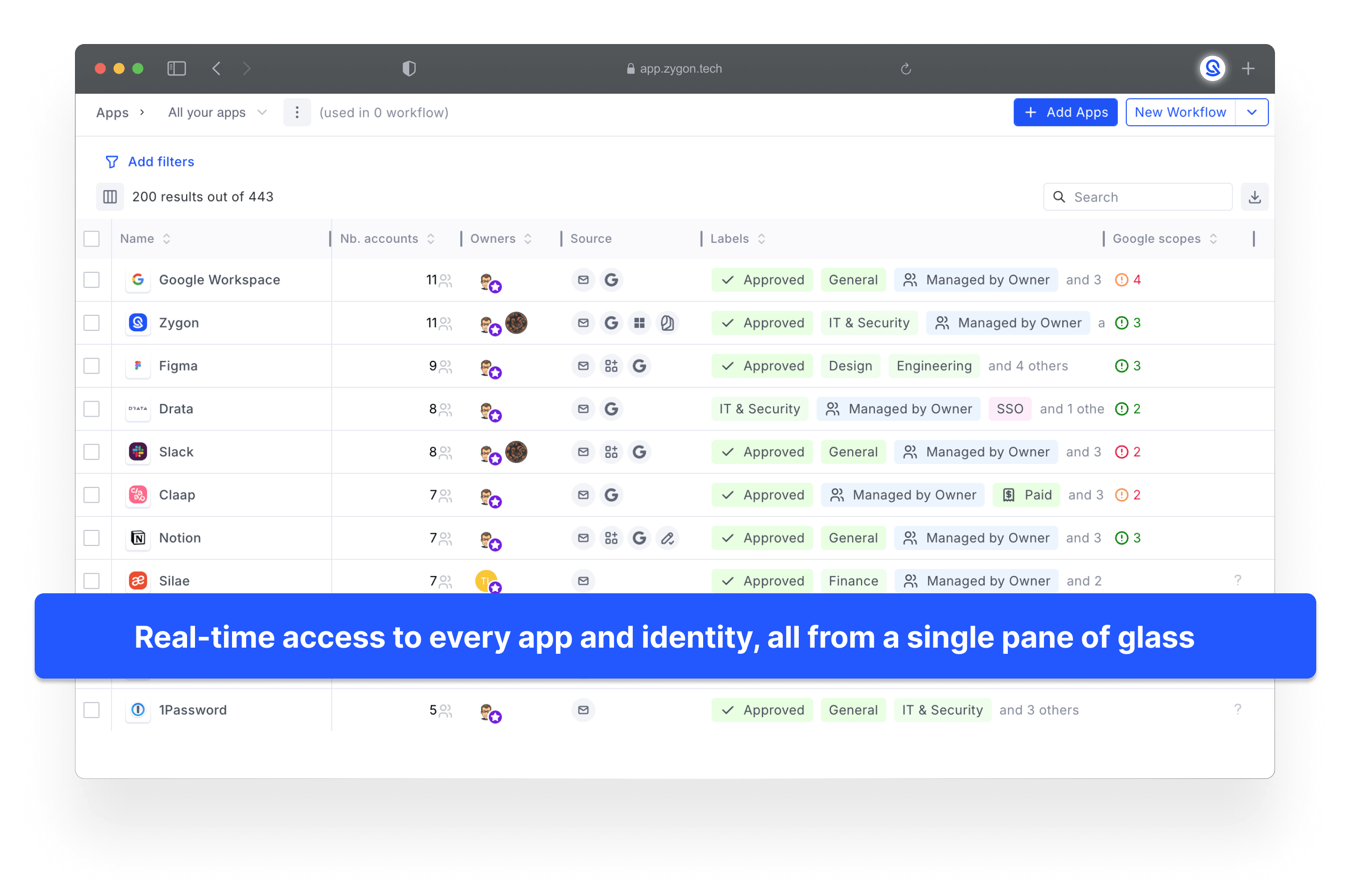
Detection takes less than an hour and is updated in real-time. This provides Security teams with the most accurate and detailed view of their organization's identity landscape, complete with granular information and advanced filtering options.
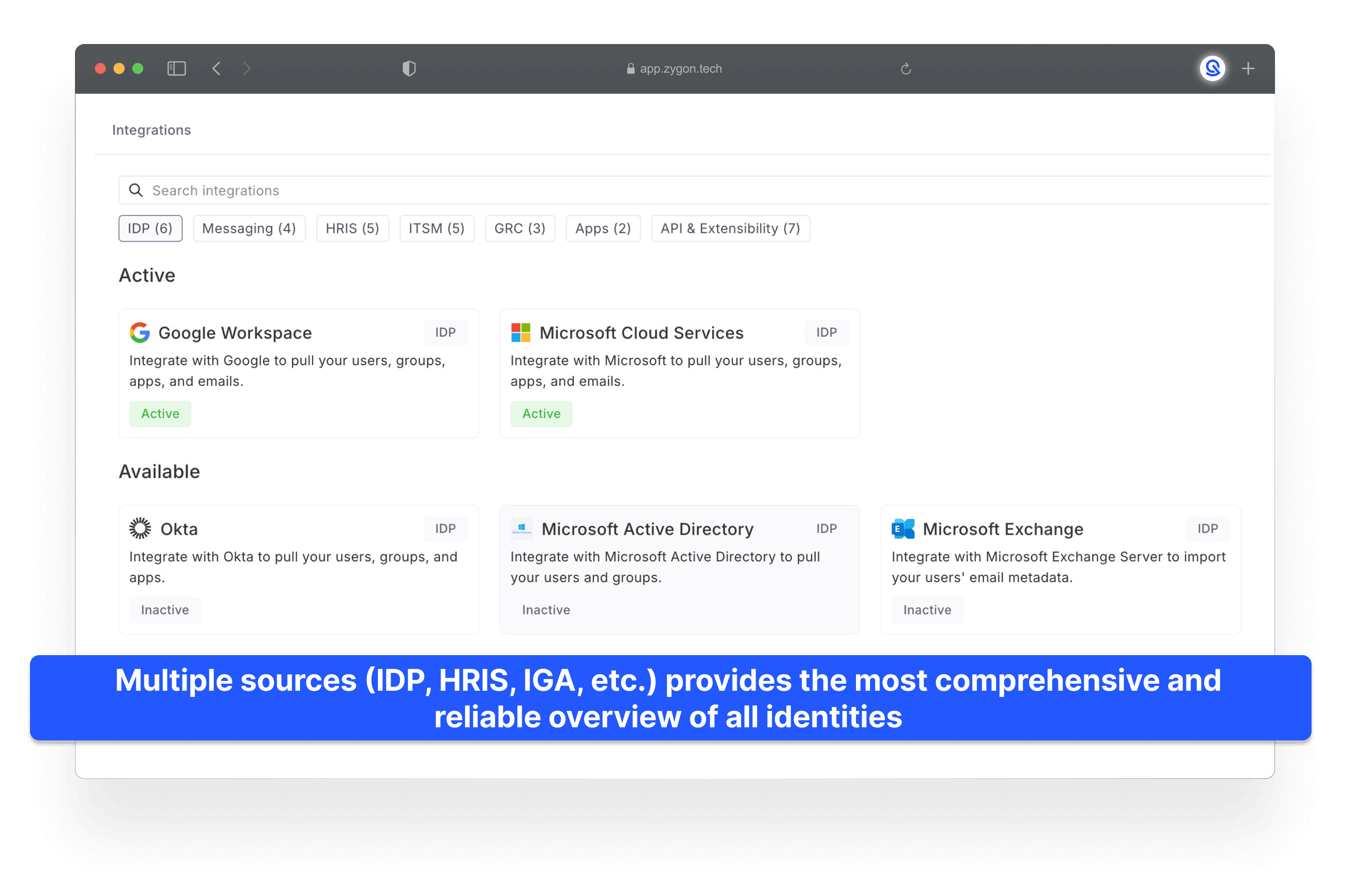
How is this achieved? It combines email metadata analysis to identify billing contacts and app owners, integrates natively with Identity Providers to access OAuth scopes and revoke tokens, and supports any tool (HRIS, ITSM, IGA, etc.), whether cloud-hosted or on-premises, via a Command Line Interface (CLI). This flexibility allows you to run Cron jobs or any tasks as needed.
Mapping identities across existing tools used to streamline access management tasks
Usually, crown-jewel apps are well-known and effectively managed behind your IdPs (Okta, Entra, Google). However, for the 80% SCIM-incompatible solutions or apps lacking premium SSO features, app owners typically handle access hygiene (manually) for their teams.
In this case, most organizations track joiner-mover-leaver (JML) movements through their helpdesk.
By the way, if you've never assessed how much time these small tasks accumulate over a year, check out this post estimating the cost of deprovisioning. You'll discover that it exceeds the workload of two full-time employees for an organization with just 1,000 staff members.
Back to the helpdesk, all you want to avoid is to overwhelm the IT team (and yourself) with low value-added tedious tasks. And once you have the right process in place, there's a reluctance to change it—a truly pressing issue, isn’t it?
There's no need to fix what isn't broken. Once you have a clear mapping of all identities in Zygon and have labeled them according to the tools they're managed in, there's no need for replacements.
But there’s still room for improvement!
Zygon provides versatile workflow capabilities, allowing you to either script directly within the platform or build workflows using our user-friendly interface.
You’re all set to eliminate unnecessary helpdesk tasks, and streamline the management of disconnected apps.
This sets the stage for smooth and efficient compliance audits.
Let's explore how!
Security & Compliance made easy with continuous monitoring
Do you have compliance requirements for identity management or app inventory (e.g., ISO, SOC2, HIPAA)?
Most of the time, it’s a solid yes. This affirmation, however, often comes with vivid memories of tedious manual tasks and the exhausting back-and-forth with other teams and app owners 🥲
That’s why you don’t want to imagine expanding the scope of user access reviews to even a small portion of all disconnected apps. Again, we feel for you.
Thanks to Zygon’s continuous monitoring of every app, discrepancies are highlighted in real time giving you the flexibility to remediate issues quickly.
The positive aspect is: transitioning from occasional rushes to continuous monitoring of app access makes the process of user access reviews a breeze.
All you need to do is export, with just a few clicks, the logs saved on Zygon that have everything recorded.
Cherry on the cake: our browser extension allows you to detect, record and/or block questionable apps in real-time that users might be tempted to use—after all, you can't expect them to read all the security guidelines, can you?
Conclusion
The journey of identity governance is continuous and dynamic, shaped by unique organizational needs and an ever-changing technological environment.
Feedback from the field has highlighted significant challenges faced by IAM practitioners. The deployment of legacy IGA platforms is slow and limited to a limited portion of the apps used within their organization.
These disconnected apps make it difficult to clarify ownership and streamline access-related tasks.
Zygon acts as a complementary platform that bridges this gap and equips IAM practitioners with the capabilities they need to release the pressure on IT helpdesk and streamline compliance audits.
Struggling with user access reviews?
Get your free guideFAQ
All the questions you can have
What do you mean by "disconnected apps"?
While many applications are registered through procurement and listed in an ERP or other dedicated systems, these methods often fail to manage identities or evaluate the business criticality of these applications effectively.
This situation is best captured by the concept of "disconnected applications", which underscores identities that are neither managed within an Identity Governance and Administration (IGA) solution nor adequately maintained in your identity provider or SSO solution.
These unmanaged apps are still awaiting integration or lack SCIM support, preventing unified access from a single pane of glass. This is one of the key challenges that Zygon aims to address.